Cryptojacking is a growing risk: hackers use the resources of infected computers or mobile devices to use their resources for their encryption. In May and June 2022, Bitdefender discovered a global attack campaign in which cybercriminals exploited known vulnerabilities to load DLL files in Microsoft OneDrive Exploit it to install encryption malware on victims’ systems.
- In principle, they can download any malware via the vulnerability – including malware.
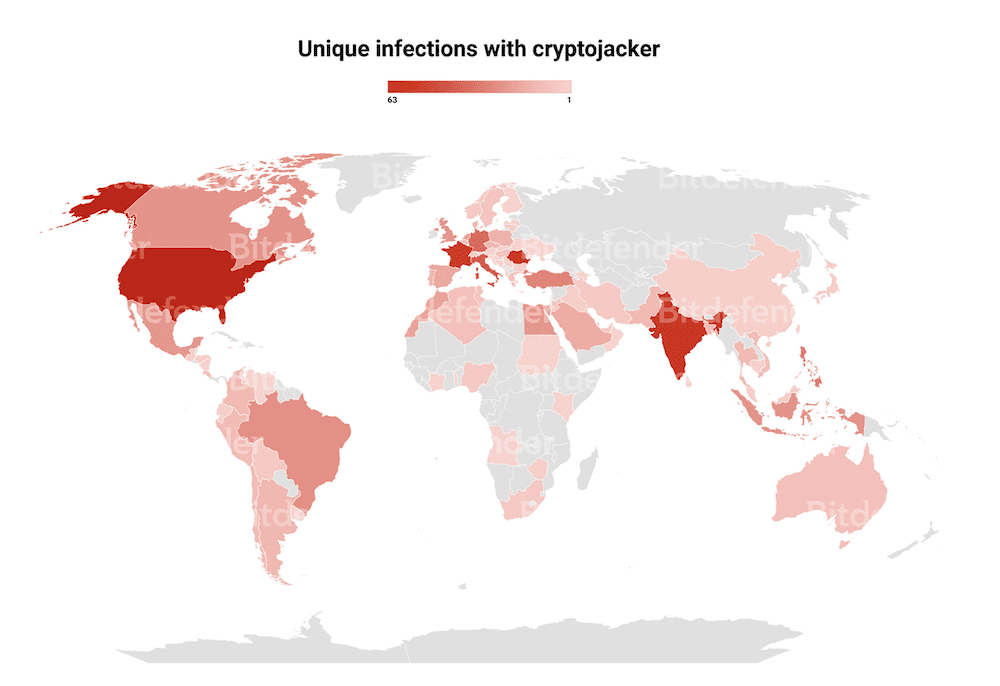
- It attacked 700 instances of Microsoft OneDrive detected by Bitdefender in May and June 2022.
- Germany is among the most affected countries worldwide
- Microsoft does not interpret DLL sideloading as a vulnerability.
- The known sideload vulnerability is also suitable for ransomware attacks or for spyware infection.
The Windows operating system and other applications are built on DLL files that provide or extend functionality. Once an application needs a function in a particular DLL, it searches for it in the predetermined order, first in the directory the application was loaded from, then in the system directory, in the 16-bit system directory, in the Windows directory, in the directory currently in use and recently in the listed directories in the path environment variable. If the full path of the required DLL files is not specified, the application will try to find the file on the given paths. If hackers implement a malicious DLL on the search path, it will silently load and run the application in place of the application that actually needs it.
Download malicious DLLs via OneDrive.exe or OneDriveStandaloneUpdater.exe
In the attack analyzed by Bitdefender, the attackers write a fake secure32.dll file to the %appdata%\Local\Microsoft\OneDrive path without special privileges. OneDrive processes OneDrive.exe or OneDriveStandaloneUpdater.exe and then loads them.
Since %appdata%\Local\Microsoft\OneDrive\OneDriveStandaloneUpdater.exe is scheduled to run daily, the fake DLL files are now still present in the victim’s system.
In addition, the attackers install the fake DLL into the system via %appdata%\Local\Microsoft\OneDrive\OneDrive.exe. You can configure OneDrive.exe to start with every reboot using the Windows registry.
After the fake secure32.dll file is loaded via those OneDrive processes, it reloads the encryption program and infects it in legitimate Windows processes.
In the same way, attackers may also install ransomware or spyware on the systems.
In the crypto campaign, hackers deployed algorithms to mine four cryptocurrencies: Etchasch in particular, as well as ethash, ton and xmr. On average, cybercriminals make a profit of $13 per infected computer. Victims notice losses in the performance of the systems.
Microsoft: Install OneDrive “per device”.
Users can Microsoft OneDrive Install either “per user” or “per device”. The default setting is “per user” installation. In this configuration, users without special privileges can write to the folder where OneDrive is located. Hackers can drop malware here, modify executable files, or completely overwrite them. Therefore, Microsoft recommends that you install OneDrive “per device”. You can find instructions on how to do this over here.

More precautions are needed
However, “per device” installation is not appropriate for every environment or every privilege level. So Bitdefender warns OneDrive users to be very careful. Both antivirus protection and the operating system used should always be up to date. Be careful when downloading cracked software or game cheats.
More information:
full study over here Available.
www.bitdefender.com

“Social media evangelist. Baconaholic. Devoted reader. Twitter scholar. Avid coffee trailblazer.”








More Stories
Longest jets in the universe discovered – giant particle streams as long as 140 Milky Way galaxies in a row
New method reveals 307 supernova remnants
Snapchat is upping the ante on augmented reality glasses