A new macOS data-stealing malware is currently circulating, and scammers are apparently selling it on relevant forums as a so-called Malware as a Service (MaaS) for a monthly fee. As security firm Cado writes, the data-stealing malware has been dubbed “Cthulhu Stealer.” The malware is designed to steal important data from your Mac.
advertisement
Pretends to be a popular app
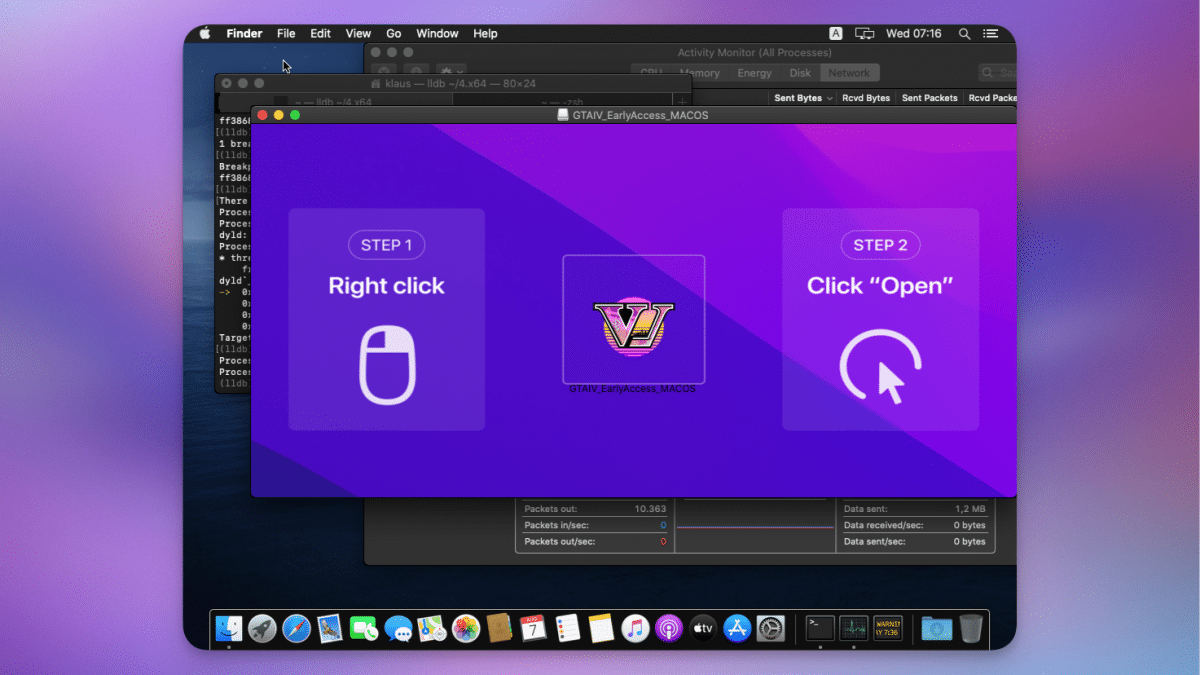
The new stealth tool is being circulated in the form of various applications designed to lure users into clicking – including a supposed GTA VI preview (which, amusingly, is being distributed with the incorrect file name “GTAIV_EarlyAccess_MACOS_Release.dmg”), an Adobe Creative Cloud pirate tool or a copy of the popular cleanup tool CleanMyMac. According to Cado Security, other file names being circulated are generic ones like “Launch.dmg” or “Setup2024.dmg.”
Cthulhu Stealer is said to have been trading in various forms and under different names since 2023 and is regularly updated as a MaaS for “customers.” Pricing is said to be around $500 per month, and is offered through various forums on the dark web. The malware is suitable for Apple Silicon and Intel Mac devices. It can access data from your keychain (iCloud), browser passwords including browsing history, various cryptocurrency wallets, Telegram account data, and more, and send it to its operators. Cado Security has discovered nearly two dozen good sources of data that the thief could use if they hacked into a Mac.
Installation in several steps
After all, the malware installation process is still quite cumbersome. Users are encouraged to launch the app by right-clicking on “Open,” which in turn triggers a macOS warning dialog because the malware does not have an Apple signature. With macOS 15, opening unsigned apps should become even more difficult. Finally, Cthulhu Stealer also prompts users to “Update System Settings.”
To do this, you must enter the administrator password. This dialog also looks rather generic. According to Coda Security, the malware is written in GoLang and also uses a command line tool osascript To run AppleScript code. You will also be asked for your MetaMask password, if available. Conclusion: Cthulhu Stealer seems to be targeting more inexperienced users. Users should be careful and not run any software from questionable sources.
(Bachelor's)

“Social media evangelist. Baconaholic. Devoted reader. Twitter scholar. Avid coffee trailblazer.”







More Stories
Longest jets in the universe discovered – giant particle streams as long as 140 Milky Way galaxies in a row
New method reveals 307 supernova remnants
Snapchat is upping the ante on augmented reality glasses